Securosys CloudHSM


Challenge
Running a Hardware Security Module (HSM) demands substantial expertise, resources, and adherence to stringent security protocols. However, for many organizations, managing HSMs is not a core competency. This gap between the necessity for robust security measures and the available expertise poses a significant challenge.
Solution
Our HSM as-a-service or CloudHSM provides a seamless, secure, and cost-effective path to achieving full compliance with data security requirements and regulations. Securosys CloudHSM streamlines the generation, use, and storage of encryption keys by delegating the time-consuming tasks of evaluation, setup, maintenance, and updates to our team of security experts. Thus, allowing you to focus on your core business while resting assured that robust security measures are in place.
Securosys CloudHSM operates on a patented proprietary hardware and software architecture, meticulously crafted and sustained in-house, ensuring end-to-end control without any intermediaries. It is available with dedicated HSMs, or as shared service in multi-tenancy HSMs, either as a Global or as a Regional Swiss, Europe, North America, or Asia-Pacific cluster. For redundancy and availability purposes, these HSMs are deployed in a cluster that keeps all data synchronous in multiple HSMs. With this setup, CloudHSM can offer any organization local, regional, and global HSM-clusters, providing access points in different locations, bringing latency down and offering the service in their jurisdiction.
Get the best of Securosys Primus HSM,
directly from the Cloud






Excellent price-performance ratio
Leverage a shared environment for economical operations without compromising on security. Competitive and flexible pricing options, without initial costs or tied-up capital.
Architecture built for High Security and Availability
Our service is built and hosted by the experts who developed and produced the HSMs for the Swiss payment clearing and settlement system. Securosys CloudHSM operates on a proprietary hardware and software architecture, ensuring end-to-end control without intermediaries.
Global Availability
Compatible with all major cloud service providers, Securosys CloudHSM is accessible through regional clusters in Switzerland, Germany, Singapore, the US, or globally.

How does it work?
CloudHSM is a cloud-hosted Hardware Security Module (HSM) service that enables you to perform cryptographic operations and manage encryption keys with enhanced security.
Use Cases
 PKI (Public Key Infrastructure)
The multi-tenancy of CloudHSM allows one partition to be used for the root key of the main Certificate Authority (CA), while clients can utilize additional partitions for sub-CAs. The root key signs certificates for the sub-CAs, streamlining PKI management. Securosys CloudHSM allows as well to switch the partition that holds the root key, cryptographically offline for even more security
PKI (Public Key Infrastructure)
The multi-tenancy of CloudHSM allows one partition to be used for the root key of the main Certificate Authority (CA), while clients can utilize additional partitions for sub-CAs. The root key signs certificates for the sub-CAs, streamlining PKI management. Securosys CloudHSM allows as well to switch the partition that holds the root key, cryptographically offline for even more security
 Secure Storage of Crypto Assets
CloudHSM offers secure generation and management of private keys, which are stored redundantly in an HSM cluster. This ensures that keys remain accessible even if your HSM cluster is unavailable during natural disasters, providing reliable and resilient security for crypto assets.
Learn more
Secure Storage of Crypto Assets
CloudHSM offers secure generation and management of private keys, which are stored redundantly in an HSM cluster. This ensures that keys remain accessible even if your HSM cluster is unavailable during natural disasters, providing reliable and resilient security for crypto assets.
Learn more
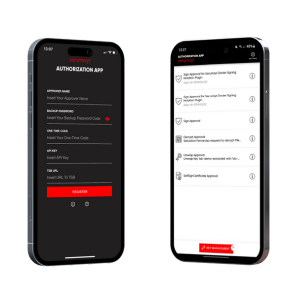
 Highly Secure Blockchain Systems
Securosys CloudHSM addresses digital signature issues in Distributed Ledger Technology (DLT) by enabling multi-signature functionality. This procedure requires at least two concurrent authorizations for each action, enhancing security.
Learn more
Highly Secure Blockchain Systems
Securosys CloudHSM addresses digital signature issues in Distributed Ledger Technology (DLT) by enabling multi-signature functionality. This procedure requires at least two concurrent authorizations for each action, enhancing security.
Learn more
 Document Signing and Archiving
CloudHSM, ISO 27001 certified and operating on Common Criteria certified Primus HSMs, supports eIDAS or ZertES compliant electronic signatures with qualified certificates. It’s certified to Common Criteria EAL4+ EN 419 221-5, and its patented SKA function ensures sole control of digital signatures. The attestation function also automates audit requirements for Trust Service Providers, simplifying the process of qualified seals.
Document Signing and Archiving
CloudHSM, ISO 27001 certified and operating on Common Criteria certified Primus HSMs, supports eIDAS or ZertES compliant electronic signatures with qualified certificates. It’s certified to Common Criteria EAL4+ EN 419 221-5, and its patented SKA function ensures sole control of digital signatures. The attestation function also automates audit requirements for Trust Service Providers, simplifying the process of qualified seals.
 Code Signing
CloudHSM seamlessly integrates into development environments, enhancing code signing automation. Using an Extended Validation (EV) Certificate from a recognized CA ensures software trustworthiness. Compliant with CA/Browser Forum standards, CloudHSM supports issuing and managing Publicly-Trusted Code Signing certificates. Key attestation further ensures keys are generated on the HSM and remain secure, adding extra integrity to your code signing process.
Code Signing
CloudHSM seamlessly integrates into development environments, enhancing code signing automation. Using an Extended Validation (EV) Certificate from a recognized CA ensures software trustworthiness. Compliant with CA/Browser Forum standards, CloudHSM supports issuing and managing Publicly-Trusted Code Signing certificates. Key attestation further ensures keys are generated on the HSM and remain secure, adding extra integrity to your code signing process.
 Identity and Access Management
CloudHSM enables secure generation and storage of keys to protect digital identities. It offers high availability, centralized security, and easy handling of various digital keys, strengthening identity and access management systems.
Identity and Access Management
CloudHSM enables secure generation and storage of keys to protect digital identities. It offers high availability, centralized security, and easy handling of various digital keys, strengthening identity and access management systems.
 Database Encryption
Encrypting your database and storing the keys centrally on CloudHSM protects your data effectively. Even if a database is stolen, the encryption keys stored on CloudHSM would prevent unauthorized access to the data.
Database Encryption
Encrypting your database and storing the keys centrally on CloudHSM protects your data effectively. Even if a database is stolen, the encryption keys stored on CloudHSM would prevent unauthorized access to the data.
FAQs
What is CloudHSM, and how does it differ from traditional HSMs?
Which server regions do you offer?
Does your CloudHSM subscription support Bitcoin and other cryptocurrencies?
How do I integrate CloudHSM with my existing applications?
Do I need to maintain any hardware or software?
What are the pricing models for CloudHSM?
What kind of support and maintenance is provided with CloudHSM?
Is your service certified?
Securosys holds my key material. Is it possible to have my own backup?
Is there a migration path from Cloud to on-premises?
Related Products
 CloudHSM Service Offerings
Our CloudHSM offerings provide versatile solutions tailored to meet diverse security needs. Multiple Solution Architectures cover most of the requirements and with over 30 pre-configured and well-documented services
CloudHSM Service Offerings
Our CloudHSM offerings provide versatile solutions tailored to meet diverse security needs. Multiple Solution Architectures cover most of the requirements and with over 30 pre-configured and well-documented services
 Cloud Console
Effortless setup and management of your cloud-based HSM solution, through a fast, user-friendly cloud console.
Cloud Console
Effortless setup and management of your cloud-based HSM solution, through a fast, user-friendly cloud console.
 HSM Overview
Our Primus HSM guarantees secure generation, storage, and management of digital identities, encryption keys, and assets.
HSM Overview
Our Primus HSM guarantees secure generation, storage, and management of digital identities, encryption keys, and assets.
data protection with full access to our cloud-based HSM services.